3 Identity Links: Rule 34
"If it exists, there is porn of it"
First, an update on my last post. I said “we need standardized infrastructure something like” Microsoft’s OBO OAuth profile. I was remiss in not linking to this individual IETF Internet-Draft from WSO2, OAuth 2.0 Extension: On-Behalf-Of User Authorization for AI Agents, dating from a few weeks ago, which could end up on such a track at some point. Its flow has a “requesting party” feel, and its authors are participating in the OpenID Foundation’s new AI Identity Management community group, where some great discussions are already happening.
Now let’s get to a fresh crop of links! I promise I’ll explain today’s title.
NOTE: If you’re not familiar with Internet Rule 34, expect NSFW search results…
Facial age estimation and #onlineporn
Published by Robin Tombs at LinkedIn1 on July 14, 2025
There it is. With all the discussion of age assurance and age verification, references to (what I feel compelled to type as) pr0n are popping up all over the place — and seeing this as a hashtag on LinkedIn gave me pause. It’s a great use case. While my SXSW talk pointed to proposed age verification laws for dieting and skincare products, honestly pr0n is sort of THE use case for age testing. Even though people don’t inherently want to be age-tested for any product, given Rule 34 and its accompanying regulation, is pr0n gated by privacy-preserving age estimation the killer use case for consumer-driven verifiable credentials?
This means the majority of individuals won’t need to repeatedly use ID Docs, credit cards, Name+DoB+Address to prove age at thousands of websites & apps where age checks are increasingly required.
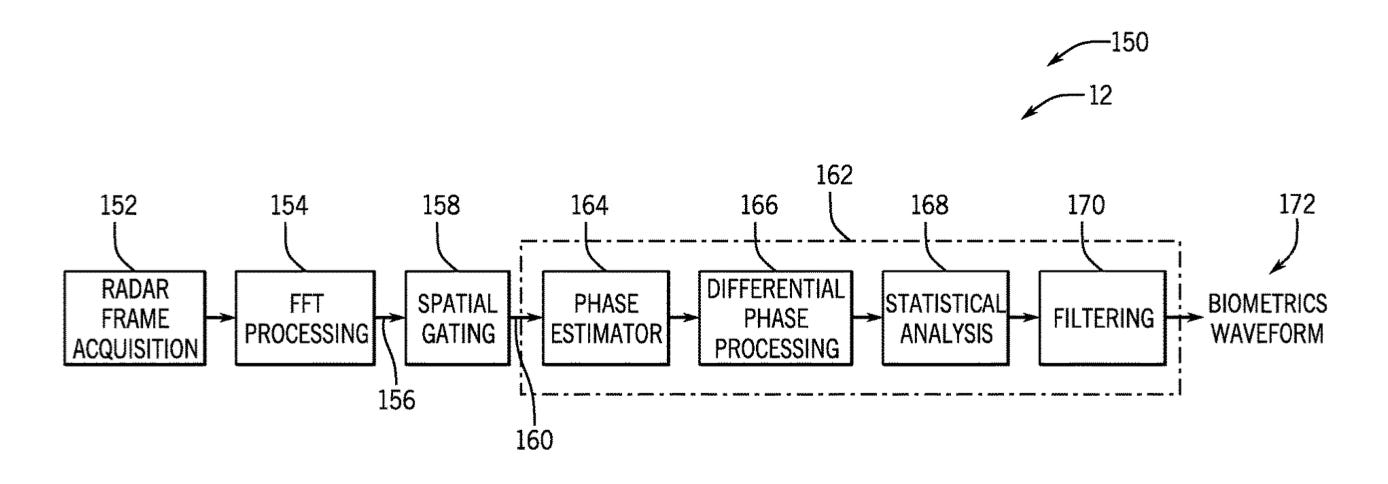
Apple wins a patent for Apple devices with Radar-Based Biometrics that could detect Heartbeats, rate of Breathing, Tremors, Seizures & more
Published by Patently Apple on July 1, 2025; h/t Gabriel Steele on LinkedIn; patent here
News of this and related patent applications broke a couple of years ago. Now radar-based biometrics are even closer to reality. The opportunities for passive health micro-monitoring are exciting; as a participant in the longevity movement, I hope we will all be able to benefit.
Gabe also points out opportunities for fraud detection — and naturally his comment thread also turns to discussions of privacy. This is your regular reminder that even with selective disclosure through wallets, correlation and linkability are never far away…so keep reading for my thoughts on a proposed solution.
(I will leave any connection between items no. 1 and no. 2 as an exercise for the reader!)
Musings of a Trust Architect: When Technical Standards Meet Geopolitical Reality
Published by Christopher Allen at Blockchain Commons
Commenting on the recent Global Digital Collaboration conference, Chris amply documents how, despite many years of effort, his own very much included:
Supposedly self-sovereign certificates phoning home whenever they’re accessed is another recent threat that demonstrates best intentions gone awry. This not only violates privacy, but it undercuts some of our best arguments for self-sovereign control of credentials by returning liability for data leaks to the issuer. The No Phone Home initiative that Blockchain Commons joined last month represents one attempt to push back on that, but it feels like plugging holes in a dam that’s already cracking. It all does.
(I commented on NoPhoneHome similarly here.)
Chris’s take is thoughtful and detailed. My take is that the reigning dynamic is constant pressure towards centralization. This is much broader than public- or private-sector imperfections; it explains SaaS, crypto exchanges, and a lot more. I gave a talk at Identiverse 2023 called Can Subsidiarity Save Decentralization?, explaining that subsidiarity is the principle of keeping governance as hyperlocal as possible.
My premise was that although digital decentralization is not cost-free, insidious re-centralization could be battled with transparency about the closeness of relationships among the online entities you’re interacting with, to let you optimize the alignment of others’ interests with your own. It seemed very abstruse at the time.
The talk isn’t online — though I’m happy to share the slides if you drop me a note. But a fresh search shows a recent spate of real research on the topic.
Chris concludes with:
Perhaps it’s time for a new architecture: one that acknowledges these inversions and builds resistance into its very foundations.
I agree — but we should be cautious of creeping hubris that says we can easily out-game such persistent patterns.
Thanks for reading! What’s your take?
In other news, I’ll be appearing with my Persona-Driven Identity coauthor Jacob Ideji on Mike Schwartz’s Identerati Office Hours show on Tuesday, July 22 — hope you can tune in live! You can get the white paper free through the episode page, and you can always check out my News page to catch forthcoming appearances.
I have a feeling everyone who reads this can access LinkedIn posts, but if it poses logistical problems, let me know.



is decentralization worth saving? or is it just the road to anarchy. People do want freedom of action, but is that necessarily incompatible with centralization of a common set of rules. Clearly Stalin wanted centalization, pushed hard to enable centralization of control and it failed him.. All of Russian society wound up in misery. The network effect (Metcalfe’s Law) seems to force centalization. Does anyone think Metcalfe’s Law is not a fact?