Demystifying NIST SP 800-63
A Practical Guide for Organizations Navigating Digital Identity
I’m pleased to present this cross-post of an article I developed in collaboration with trusted vision AI leader Paravision. For more information, reach out to info@paravision.ai.
1. Introduction
NIST’s Special Publication 800-63 is a frequently referenced — and often misunderstood — document in the digital identity ecosystem. It shapes how organizations verify identities, authenticate users, and safely exchange identity information. Yet for many people, especially those outside the identity industry, NIST SP 800-63 feels complex, highly technical, and difficult to apply in real-world environments.
The goal of this article is to demystify 800-63 in clear, accessible terms without oversimplifying or glossing over the nuance that makes it important.
What is NIST 800-63 and why does it matter?
NIST is the U.S. National Institute of Standards and Technology, part of the U.S. Department of Commerce. It produces publications defining standards in many business, science, and technology realms where having an official “yardstick” is useful, from plumbing pressure-loss measurements to the viscosity of chemical elements.
Somewhere in the middle, we find the topics of Cybersecurity and Privacy and Information Technology. NIST Special Publication 800-63 is related to both.
SP 800-63, Digital Identity Guidelines, is now in its fourth revision and is a critical contribution to defining measurable confidence — or assurance — in digital identity processes. It defines measurable levels of assurance across three areas of digital identity and access management:
Identity: How confidently you know the person is who they say they are
Authentication: How confidently you can trust the method a user uses to log in
Federation: How securely identity information is passed between systems (like using the SAML or OpenID Connect standard)
Organizations can use 800-63 to mitigate organizational risk by choosing among three levels that NIST assigns to systems for each of the above areas, which can roughly be categorized as low (1), medium (2), and high (3).
Who uses 800-63?
The official scope of 800-63 is limited to U.S. government information systems, but the guidelines are so useful that they’re widely applied in the private sector and even influence global enterprises.
Why is there so much confusion?
Selecting a required assurance level for specific organizational needs may seem like a simple process, and indeed it is this procedural simplicity that has led to the popularity of SP 800-63. However, meeting the requirements behind these levels is much harder. It requires a great amount of attention to technical design, user experience, and operational guardrails. Providers must also undergo rigorous conformance assessments and ongoing reviews to be certified against the assurance levels.
2. How NIST 800-63 evolved — and why It split into 63A, 63B, and 63C
Some of the confusion surrounding SP 800-63 comes from its history. Like many technical frameworks, it has evolved significantly over time.
A brief history of major updates
Originally, assurance was measured with four simple levels, referred to as levels of assurance (LOA) 1 through 4. Today, assurance is expressed across three dimensions:
Identity Assurance Level (IAL): Levels 1-3
Authentication Assurance Level (AAL): Levels 1-3
Federation Assurance Level (FAL): Levels 1-3
The first version of SP 800-63, published in 2011 and called Electronic Authentication Guideline, was simpler and addressed early identity technologies at a high level. The second version (2013) coincided with increased enterprise IAM adoption and growing appetite for interoperable identity federation.
The third version in 2017, finally called Digital Identity Guidelines, was a major shift; to reflect publicly sourced input, it introduced the three-part structure. According to NIST:
“These guidelines retire the concept of a level of assurance (LOA) as a single ordinal… Rather… agencies will select IAL, AAL, and FAL as distinct options.”
The old single-number approach could no longer capture modern identity complexity.
Version 4: the 2025 update
The fourth version (NIST SP 800-63-4) keeps the tripartite model of IAL, AAL, and FAL, while updating requirements to reflect modern identity technologies such as biometrics, identity wallets, and advanced authentication methods. These updates help organizations implement identity systems that are both secure and user-friendly, keeping pace with evolving threats and technology.
The three parts of the publication are:
63A: Identity proofing – Guidelines for verifying that a user is who they claim to be.
63B: Authentication – Requirements for securely validating user credentials.
63C: Federation – Rules for safely sharing identity information across different systems or organizations.
How they work together
The sub-documents are designed to be used in combination. A typical workflow (shown in the below diagram) might look like this: an organization first verifies a user’s identity (Step 1: 63A), then ensures the user can authenticate securely (Step 4: 63B), and finally, if identity data is shared with partners, applies federation controls (Step 5: 63C) to maintain trust across systems.
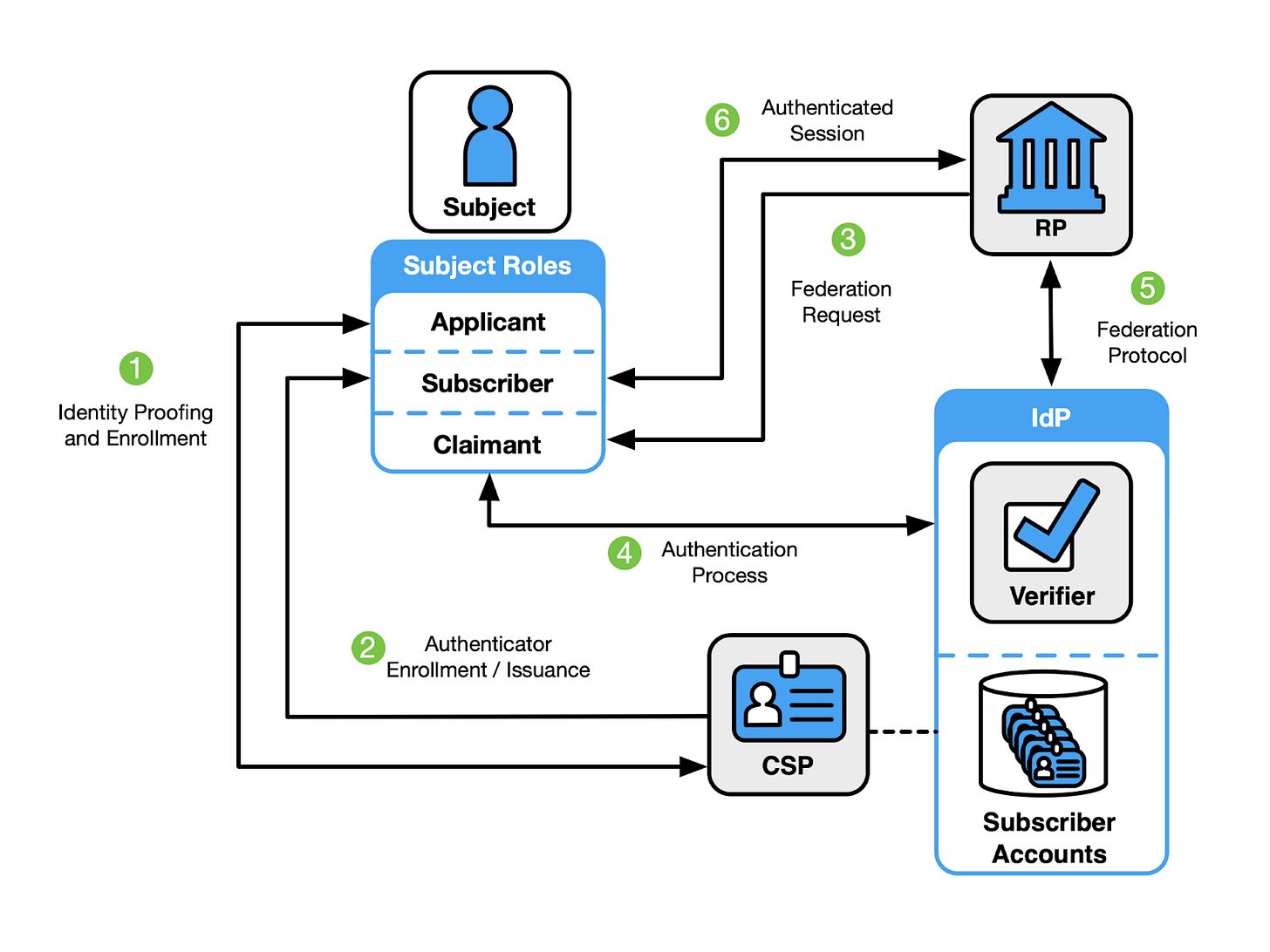
It’s important to note that organizations don’t have to match assurance levels across all three dimensions. For example, they might choose a lighter identity proofing (IAL1) together with stronger authentication (AAL3). In practice, many organizations end up choosing aligned levels across touchpoints, and IAL2 and AAL2 often emerge as practical “sweet spots” due to feasibility and certification availability.
3. Key Concepts: IAL, AAL, FAL — What They Mean in the Real World
The persistent question in online services, apps, and human interactions is: Has the other side earned my trust? Is it safe to interact with them or do business with them? In real terms: Is this user actually the person they claim to be? Do we know enough about this traveler to keep everyone else safe? Am I interacting with a human or a bot?
Because digital systems today have many moving parts, the supply chain of identification can be long and complex. This is why NIST defines three separate types of measurements:
IAL (Identity Assurance): Do the user’s security credentials connect to a legitimate real-world human being?
AAL (Authentication Assurance): How likely is it that the user’s credentials have been stolen?
FAL (Federation Assurance): How trustworthy is the exchange of identity information across systems?
How organizations apply the levels
Organizations looking to leverage these assurance promises typically get support from vendors specializing in high-assurance systems, artifacts, and processes. The Kantara Initiative performs certification work to approve ecosystem participants at IAL2 and AAL2, which allows these providers to use a trust mark signaling their capabilities.
Negotiations and agreements around assurance usually take place in:
Business contracts
Trust frameworks
Operational policies
4. Navigating the Standards Ecosystem
An organization operating across multiple jurisdictions or sectors may encounter assurance requirements that don’t map neatly to each other. While this risk is lower today thanks to NIST’s influence and the adoption of standards globally, true conflicts can still arise — for example, when authenticating minors, complying with local biometrics laws, or meeting detailed user experience requirements like those in UK Open Banking.
In these cases, a good approach is to aim for a “high-water mark”: the strongest assurance requirement across all applicable frameworks. While SP 800-63 doesn’t define the use of finer-grained levels, like “IAL2.7”, organizations can adjust their internal policies and processes to get as close as possible to meeting multiple parties’ requirements.
Emerging trends to watch
NIST SP 800-63 revision 4 took years to produce, so another full revision isn’t expected soon. However, just over a year before it was finalized, NIST published a supplement providing interim guidance on emerging passkey technology.
We can expect NIST to release more supplements in future to keep pace with fast-moving areas. For instance, innovations in AI agent security or new threats like injection attacks may require similar interim guidance.
5. FAQs and Common Misunderstandings
NIST has published a Frequently Asked Questions list with answers, and enables the public to ask additional questions.
What are common mistakes organizations make when interpreting the standard?
A common misconception organizations make is that the three assurance dimensions — IAL, AAL, and FAL — must always match numerically. In some cases, perfect alignment can be appropriate, but it’s often unnecessary. For instance, an organization might choose lightweight identity verification (IAL1) combined with strong authentication (AAL3). This approach ensures that the user is strongly authenticated without having to handle sensitive identity verification data when it isn’t required.
How can buyers avoid jargon overload?
When in doubt, organizations should focus first on the real business risks they are trying to mitigate, then seek to understand how the assurance levels might help them mitigate that risk.
Closing Thoughts: Key Takeaways on NIST 800-63
NIST SP 800-63 provides a practical framework for measuring confidence in digital identity. By separating assurance into three dimensions — Identity Assurance (IAL), Authentication Assurance (AAL), and Federation Assurance (FAL) — it allows organizations to apply nuanced levels of risk management rather than a one-size-fits-all approach.
A few key points to remember:
Start with business risk, not technology. Identify what you’re trying to protect, then select assurance levels that help mitigate those risks.
Levels don’t always have to match. Lightweight identity proofing (IAL1) can be paired with strong authentication (AAL3) where appropriate. In practice, IAL2 and AAL2 often hit the “sweet spot” of feasible implementation, risk reduction, and certification availability.
Implementation is more complex than selection. Achieving certified assurance levels requires careful attention to technical systems, operational processes, and user experience.
Ongoing evolution matters. Supplements and interim guidance allow organizations to adopt emerging technologies, like cloud-syncable passkeys or AI-related security measures, without waiting for a full SP 800-63 revision.
Ultimately, SP 800-63 is designed to help organizations make smarter, risk-based decisions about digital identity, whether in government, private enterprise, or cross-sector contexts. Understanding how the three assurance dimensions interact and how to apply them in the real world is the key to confidently navigating today’s complex digital identity landscape.
I hope you enjoyed this installment of The Workshop. It’s part of a larger conversation about the future of identity and how to make it — in a word — irresistible. I hope you’ll subscribe as we continue to push the edges of the envelope here at Venn Factory.





“Because digital systems today have many moving parts, the supply chain of identification can be long and complex.”
You’re not kidding lol!!
Great post, always nice to see these topics made approachable. Thanks.